Auditd es uno de esos servicios de Linux con los que puedes tener una bonita relación de amor, odio a partes iguales, pero en cualquier caso, siempre es recomendable tenerlo activo en tu sistema, y, sobre todo, tener unas buenas reglas de auditoría de tu sistema. Te voy a contar cómo instalarlo en Rocky Linux 9 y que reglas estoy usando yo.
- Puedes ver otras cosas que he hecho en el servidor en la entrada: Cómo montar un servidor Linux en Linode Akamai.
Instalación
Probablemente, ya tengas instalado el paquete en Rocky Linux, pero siempre lo puedes comprobar con:
sudo dnf install auditLo que no vas a tener instalado, porque no todo el mundo lo necesita, son sus plugins para mandar esos logs a sistemas externos o a syslog (no lo he hecho).
sudo dnf install audispd-plugins- El archivo de configuración lo tienes en /etc/audit/auditd.conf, pero en principio no vamos a cambiar nada. El log que puedes consultar con los eventos está en /var/log/audit/audit.log.
Ahora tienes que activar el daemon para que se inicie con el sistema y luego conseguir que auditd empiece a recopilar información:
sudo systemctl enable auditd
sudo service auditd startPero el problema es que ahora tienes el sistema en marcha sin ninguna regla. Auditd no sabe qué eventos tiene que registrar de tu sistema. Se lo tienes que decir.
Configuración
Puedes añadir reglas temporales al sistema con el comando auditctl y con este formato:
auditctl -w ruta_archivo -p permisos -k key_name (nombre)Pero son reglas temporales que se te van a marchar al cielo de las reglas de Linux en cuanto hagas un reboot del sistema.
Para que sean persistentes, todas las reglas las vas a tener que meter en el siguiente directorio /etc/audit/rules.d/, por ejemplo creando el archivo /etc/audit/rules.d/audit.rules.
#Creamos el archivo de reglas
vi /etc/audit/rules.d/audit.rules
#Entramos en modo inserción pulsando la letra iY podemos utilizar las siguientes reglas, que prácticamente son un estándar desde el que puedes comenzar a utilizar Auditd (https://github.com/Neo23x0/auditd):
# ___ ___ __ __
# / | __ ______/ (_) /_____/ /
# / /| |/ / / / __ / / __/ __ /
# / ___ / /_/ / /_/ / / /_/ /_/ /
# /_/ |_\__,_/\__,_/_/\__/\__,_/
#
# Linux Audit Daemon - Best Practice Configuration
# /etc/audit/audit.rules
#
# Compiled by Florian Roth
#
# Created : 2017/12/05
# Modified : 2023/01/25
#
# Based on rules published here:
# Gov.uk auditd rules
# https://github.com/gds-operations/puppet-auditd/pull/1
# CentOS 7 hardening
# https://highon.coffee/blog/security-harden-centos-7/#auditd---audit-daemon
# Linux audit repo
# https://github.com/linux-audit/audit-userspace/tree/master/rules
# Auditd high performance linux auditing
# https://linux-audit.com/tuning-auditd-high-performance-linux-auditing/
#
# Further rules
# For PCI DSS compliance see:
# https://github.com/linux-audit/audit-userspace/blob/master/rules/30-pci-dss-v31.rules
# For NISPOM compliance see:
# https://github.com/linux-audit/audit-userspace/blob/master/rules/30-nispom.rules
# Remove any existing rules
-D
# Buffer Size
## Feel free to increase this if the machine panic's
-b 8192
# Failure Mode
## Possible values: 0 (silent), 1 (printk, print a failure message), 2 (panic, halt the system)
-f 1
# Ignore errors
## e.g. caused by users or files not found in the local environment
-i
# Self Auditing ---------------------------------------------------------------
## Audit the audit logs
### Successful and unsuccessful attempts to read information from the audit records
-w /var/log/audit/ -p wra -k auditlog
-w /var/audit/ -p wra -k auditlog
## Auditd configuration
### Modifications to audit configuration that occur while the audit collection functions are operating
-w /etc/audit/ -p wa -k auditconfig
-w /etc/libaudit.conf -p wa -k auditconfig
-w /etc/audisp/ -p wa -k audispconfig
## Monitor for use of audit management tools
-w /sbin/auditctl -p x -k audittools
-w /sbin/auditd -p x -k audittools
-w /usr/sbin/auditd -p x -k audittools
-w /usr/sbin/augenrules -p x -k audittools
## Access to all audit trails
-a always,exit -F path=/usr/sbin/ausearch -F perm=x -k audittools
-a always,exit -F path=/usr/sbin/aureport -F perm=x -k audittools
-a always,exit -F path=/usr/sbin/aulast -F perm=x -k audittools
-a always,exit -F path=/usr/sbin/aulastlogin -F perm=x -k audittools
-a always,exit -F path=/usr/sbin/auvirt -F perm=x -k audittools
# Filters ---------------------------------------------------------------------
### We put these early because audit is a first match wins system.
## Ignore current working directory records
-a always,exclude -F msgtype=CWD
## Cron jobs fill the logs with stuff we normally don't want (works with SELinux)
-a never,user -F subj_type=crond_t
-a never,exit -F subj_type=crond_t
## This prevents chrony from overwhelming the logs
-a never,exit -F arch=b64 -S adjtimex -F auid=-1 -F uid=chrony -F subj_type=chronyd_t
## This is not very interesting and wastes a lot of space if the server is public facing
-a always,exclude -F msgtype=CRYPTO_KEY_USER
## Open VM Tools
-a exit,never -F arch=b64 -S all -F exe=/usr/bin/vmtoolsd
## High Volume Event Filter (especially on Linux Workstations)
-a never,exit -F arch=b64 -F dir=/dev/shm -k sharedmemaccess
-a never,exit -F arch=b64 -F dir=/var/lock/lvm -k locklvm
## FileBeat
-a never,exit -F arch=b64 -F path=/opt/filebeat -k filebeat
## More information on how to filter events
### https://access.redhat.com/solutions/2482221
# Rules -----------------------------------------------------------------------
## Kernel parameters
-w /etc/sysctl.conf -p wa -k sysctl
-w /etc/sysctl.d -p wa -k sysctl
## Kernel module loading and unloading
-a always,exit -F perm=x -F auid!=-1 -F path=/sbin/insmod -k modules
-a always,exit -F perm=x -F auid!=-1 -F path=/sbin/modprobe -k modules
-a always,exit -F perm=x -F auid!=-1 -F path=/sbin/rmmod -k modules
-a always,exit -F arch=b64 -S finit_module -S init_module -S delete_module -F auid!=-1 -k modules
## Modprobe configuration
-w /etc/modprobe.conf -p wa -k modprobe
-w /etc/modprobe.d -p wa -k modprobe
## KExec usage (all actions)
-a always,exit -F arch=b64 -S kexec_load -k KEXEC
## Special files
-a always,exit -F arch=b64 -S mknod -S mknodat -k specialfiles
## Mount operations (only attributable)
-a always,exit -F arch=b64 -S mount -S umount2 -F auid!=-1 -k mount
### NFS mount
-a always,exit -F path=/sbin/mount.nfs -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
-a always,exit -F path=/usr/sbin/mount.nfs -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
## Change swap (only attributable)
-a always,exit -F arch=b64 -S swapon -S swapoff -F auid!=-1 -k swap
## Time
-a always,exit -F arch=b64 -F uid!=ntp -S adjtimex -S settimeofday -S clock_settime -k time
### Local time zone
-w /etc/localtime -p wa -k localtime
## Stunnel
-w /usr/sbin/stunnel -p x -k stunnel
-w /usr/bin/stunnel -p x -k stunnel
## Cron configuration & scheduled jobs
-w /etc/cron.allow -p wa -k cron
-w /etc/cron.deny -p wa -k cron
-w /etc/cron.d/ -p wa -k cron
-w /etc/cron.daily/ -p wa -k cron
-w /etc/cron.hourly/ -p wa -k cron
-w /etc/cron.monthly/ -p wa -k cron
-w /etc/cron.weekly/ -p wa -k cron
-w /etc/crontab -p wa -k cron
-w /var/spool/cron/ -p wa -k cron
## User, group, password databases
-w /etc/group -p wa -k etcgroup
-w /etc/passwd -p wa -k etcpasswd
-w /etc/gshadow -k etcgroup
-w /etc/shadow -k etcpasswd
-w /etc/security/opasswd -k opasswd
## Sudoers file changes
-w /etc/sudoers -p wa -k actions
-w /etc/sudoers.d/ -p wa -k actions
## Passwd
-w /usr/bin/passwd -p x -k passwd_modification
## Tools to change group identifiers
-w /usr/sbin/groupadd -p x -k group_modification
-w /usr/sbin/groupmod -p x -k group_modification
-w /usr/sbin/addgroup -p x -k group_modification
-w /usr/sbin/useradd -p x -k user_modification
-w /usr/sbin/userdel -p x -k user_modification
-w /usr/sbin/usermod -p x -k user_modification
-w /usr/sbin/adduser -p x -k user_modification
## Login configuration and information
-w /etc/login.defs -p wa -k login
-w /etc/securetty -p wa -k login
-w /var/log/faillog -p wa -k login
-w /var/log/lastlog -p wa -k login
-w /var/log/tallylog -p wa -k login
## Network Environment
### Changes to hostname
-a always,exit -F arch=b64 -S sethostname -S setdomainname -k network_modifications
### Detect Remote Shell Use
-a always,exit -F arch=b64 -F exe=/bin/bash -F success=1 -S connect -k "remote_shell"
-a always,exit -F arch=b64 -F exe=/usr/bin/bash -F success=1 -S connect -k "remote_shell"
### Successful IPv4 Connections
-a always,exit -F arch=b64 -S connect -F a2=16 -F success=1 -F key=network_connect_4
### Successful IPv6 Connections
-a always,exit -F arch=b64 -S connect -F a2=28 -F success=1 -F key=network_connect_6
### Changes to other files
-w /etc/hosts -p wa -k network_modifications
-w /etc/sysconfig/network -p wa -k network_modifications
-w /etc/sysconfig/network-scripts -p w -k network_modifications
-w /etc/network/ -p wa -k network
-a always,exit -F dir=/etc/NetworkManager/ -F perm=wa -k network_modifications
### Changes to issue
-w /etc/issue -p wa -k etcissue
-w /etc/issue.net -p wa -k etcissue
## System startup scripts
-w /etc/inittab -p wa -k init
-w /etc/init.d/ -p wa -k init
-w /etc/init/ -p wa -k init
## Library search paths
-w /etc/ld.so.conf -p wa -k libpath
-w /etc/ld.so.conf.d -p wa -k libpath
## Systemwide library preloads (LD_PRELOAD)
-w /etc/ld.so.preload -p wa -k systemwide_preloads
## Pam configuration
-w /etc/pam.d/ -p wa -k pam
-w /etc/security/limits.conf -p wa -k pam
-w /etc/security/limits.d -p wa -k pam
-w /etc/security/pam_env.conf -p wa -k pam
-w /etc/security/namespace.conf -p wa -k pam
-w /etc/security/namespace.d -p wa -k pam
-w /etc/security/namespace.init -p wa -k pam
## Mail configuration
-w /etc/aliases -p wa -k mail
-w /etc/postfix/ -p wa -k mail
-w /etc/exim4/ -p wa -k mail
## SSH configuration
-w /etc/ssh/sshd_config -k sshd
-w /etc/ssh/sshd_config.d -k sshd
## root ssh key tampering
-w /root/.ssh -p wa -k rootkey
# Systemd
-w /bin/systemctl -p x -k systemd
-w /etc/systemd/ -p wa -k systemd
-w /usr/lib/systemd -p wa -k systemd
## https://systemd.network/systemd.generator.html
-w /etc/systemd/system-generators/ -p wa -k systemd_generator
-w /usr/local/lib/systemd/system-generators/ -p wa -k systemd_generator
-w /usr/lib/systemd/system-generators -p wa -k systemd_generator
-w /etc/systemd/user-generators/ -p wa -k systemd_generator
-w /usr/local/lib/systemd/user-generators/ -p wa -k systemd_generator
-w /lib/systemd/system-generators/ -p wa -k systemd_generator
## SELinux events that modify the system's Mandatory Access Controls (MAC)
-w /etc/selinux/ -p wa -k mac_policy
## Critical elements access failures
-a always,exit -F arch=b64 -S open -F dir=/etc -F success=0 -k unauthedfileaccess
-a always,exit -F arch=b64 -S open -F dir=/bin -F success=0 -k unauthedfileaccess
-a always,exit -F arch=b64 -S open -F dir=/sbin -F success=0 -k unauthedfileaccess
-a always,exit -F arch=b64 -S open -F dir=/usr/bin -F success=0 -k unauthedfileaccess
-a always,exit -F arch=b64 -S open -F dir=/usr/sbin -F success=0 -k unauthedfileaccess
-a always,exit -F arch=b64 -S open -F dir=/var -F success=0 -k unauthedfileaccess
-a always,exit -F arch=b64 -S open -F dir=/home -F success=0 -k unauthedfileaccess
-a always,exit -F arch=b64 -S open -F dir=/srv -F success=0 -k unauthedfileaccess
## Process ID change (switching accounts) applications
-w /bin/su -p x -k priv_esc
-w /usr/bin/sudo -p x -k priv_esc
## Power state
-w /sbin/shutdown -p x -k power
-w /sbin/poweroff -p x -k power
-w /sbin/reboot -p x -k power
-w /sbin/halt -p x -k power
## Session initiation information
-w /var/run/utmp -p wa -k session
-w /var/log/btmp -p wa -k session
-w /var/log/wtmp -p wa -k session
## Discretionary Access Control (DAC) modifications
-a always,exit -F arch=b64 -S chmod -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S chown -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S fchmod -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S fchmodat -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S fchown -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S fchownat -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S fremovexattr -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S fsetxattr -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S lchown -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S lremovexattr -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S lsetxattr -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S removexattr -F auid>=1000 -F auid!=-1 -k perm_mod
-a always,exit -F arch=b64 -S setxattr -F auid>=1000 -F auid!=-1 -k perm_mod
# Special Rules ---------------------------------------------------------------
## Reconnaissance
-w /usr/bin/whoami -p x -k recon
-w /usr/bin/id -p x -k recon
-w /bin/hostname -p x -k recon
-w /bin/uname -p x -k recon
-w /etc/issue -p r -k recon
-w /etc/hostname -p r -k recon
## Suspicious activity
-w /usr/bin/wget -p x -k susp_activity
-w /usr/bin/curl -p x -k susp_activity
-w /usr/bin/base64 -p x -k susp_activity
-w /bin/nc -p x -k susp_activity
-w /bin/netcat -p x -k susp_activity
-w /usr/bin/ncat -p x -k susp_activity
-w /usr/bin/ss -p x -k susp_activity
-w /usr/bin/netstat -p x -k susp_activity
-w /usr/bin/ssh -p x -k susp_activity
-w /usr/bin/scp -p x -k susp_activity
-w /usr/bin/sftp -p x -k susp_activity
-w /usr/bin/ftp -p x -k susp_activity
-w /usr/bin/socat -p x -k susp_activity
-w /usr/bin/wireshark -p x -k susp_activity
-w /usr/bin/tshark -p x -k susp_activity
-w /usr/bin/rawshark -p x -k susp_activity
-w /usr/bin/rdesktop -p x -k susp_activity
-w /usr/local/bin/rdesktop -p x -k susp_activity
-w /usr/bin/wlfreerdp -p x -k susp_activity
-w /usr/bin/xfreerdp -p x -k susp_activity
-w /usr/local/bin/xfreerdp -p x -k susp_activity
-w /usr/bin/nmap -p x -k susp_activity
### uftp
### https://sourceforge.net/projects/uftp-multicast/
### UFTP is an encrypted multicast file transfer program, designed to securely, reliably,
### and efficiently transfer files to multiple receivers simultaneously.
### FTP also has the capability to communicate over disjoint networks separated by one or
### more firewalls (NAT traversal) and without full end-to-end multicast capability
### (multicast tunneling) through the use of a UFTP proxy server.
### T1133_External_Remote_Services
-w /usr/bin/uftp -p x -k susp_activity
-w /usr/sbin/uftp -p x -k susp_activity
-w /lib/systemd/system/uftp.service -k susp_activity
-w /usr/lib/systemd/system/uftp.service -k susp_activity
### atftpd
### https://sourceforge.net/projects/atftp/
### https://github.com/madmartin/atftp
### atftp is a client/server implementation of the TFTP protocol that implements RFCs 1350, 2090, 2347, 2348, 2349 and 7440.
### The server is multi-threaded and the client presents a friendly interface using libreadline.
### T1133_External_Remote_Services
-w /usr/bin/atftpd -p x -k susp_activity
-w /usr/sbin/atftpd -p x -k susp_activity
-w /usr/bin/in.tftpd -p x -k susp_activity
-w /usr/sbin/in.tftpd -p x -k susp_activity
-w /lib/systemd/system/atftpd.service -k susp_activity
-w /usr/lib/systemd/system/atftpd.service -k susp_activity
-w /lib/systemd/system/atftpd.socket -k susp_activity
-w /usr/lib/systemd/system/atftpd.socket -k susp_activity
## sssd
-a always,exit -F path=/usr/libexec/sssd/p11_child -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
-a always,exit -F path=/usr/libexec/sssd/krb5_child -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
-a always,exit -F path=/usr/libexec/sssd/ldap_child -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
-a always,exit -F path=/usr/libexec/sssd/selinux_child -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
-a always,exit -F path=/usr/libexec/sssd/proxy_child -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
## vte-2.91
-a always,exit -F path=/lib64/vte-2.91/gnome-pty-helper -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
-a always,exit -F path=/usr/lib64/vte-2.91/gnome-pty-helper -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
## T1002 Data Compressed
-w /usr/bin/zip -p x -k Data_Compressed
-w /usr/bin/gzip -p x -k Data_Compressed
-w /usr/bin/tar -p x -k Data_Compressed
-w /usr/bin/bzip2 -p x -k Data_Compressed
-w /usr/bin/lzip -p x -k Data_Compressed
-w /usr/local/bin/lzip -p x -k Data_Compressed
-w /usr/bin/lz4 -p x -k Data_Compressed
-w /usr/local/bin/lz4 -p x -k Data_Compressed
-w /usr/bin/lzop -p x -k Data_Compressed
-w /usr/local/bin/lzop -p x -k Data_Compressed
-w /usr/bin/plzip -p x -k Data_Compressed
-w /usr/local/bin/plzip -p x -k Data_Compressed
-w /usr/bin/pbzip2 -p x -k Data_Compressed
-w /usr/local/bin/pbzip2 -p x -k Data_Compressed
-w /usr/bin/lbzip2 -p x -k Data_Compressed
-w /usr/local/bin/lbzip2 -p x -k Data_Compressed
-w /usr/bin/pixz -p x -k Data_Compressed
-w /usr/local/bin/pixz -p x -k Data_Compressed
-w /usr/bin/pigz -p x -k Data_Compressed
-w /usr/local/bin/pigz -p x -k Data_Compressed
-w /usr/bin/unpigz -p x -k Data_Compressed
-w /usr/local/bin/unpigz -p x -k Data_Compressed
-w /usr/bin/zstd -p x -k Data_Compressed
-w /usr/local/bin/zstd -p x -k Data_Compressed
## Added to catch netcat on Ubuntu
-w /bin/nc.openbsd -p x -k susp_activity
-w /bin/nc.traditional -p x -k susp_activity
## Sbin suspicious activity
-w /sbin/iptables -p x -k sbin_susp
-w /sbin/ip6tables -p x -k sbin_susp
-w /sbin/ifconfig -p x -k sbin_susp
-w /usr/sbin/arptables -p x -k sbin_susp
-w /usr/sbin/ebtables -p x -k sbin_susp
-w /sbin/xtables-nft-multi -p x -k sbin_susp
-w /usr/sbin/nft -p x -k sbin_susp
-w /usr/sbin/tcpdump -p x -k sbin_susp
-w /usr/sbin/traceroute -p x -k sbin_susp
-w /usr/sbin/ufw -p x -k sbin_susp
### kde4
-a always,exit -F path=/usr/libexec/kde4/kpac_dhcp_helper -F perm=x -F auid>=1000 -F auid!=4294967295 -k T1078_Valid_Accounts
-a always,exit -F path=/usr/libexec/kde4/kdesud -F perm=x -F auid>=1000 -F auid!=4294967295 -k T1078_Valid_Accounts
## dbus-send invocation
### may indicate privilege escalation CVE-2021-3560
-w /usr/bin/dbus-send -p x -k dbus_send
-w /usr/bin/gdbus -p x -k gdubs_call
## setfiles
-a always,exit -F path=/usr/bin/setfiles -F perm=x -F auid>=500 -F auid!=4294967295 -k -F T1078_Valid_Accounts
-a always,exit -F path=/usr/sbin/setfiles -F perm=x -F auid>=500 -F auid!=4294967295 -k -F T1078_Valid_Accounts
### dbus
-a always,exit -F path=/lib64/dbus-1/dbus-daemon-launch-helper -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
-a always,exit -F path=/usr/lib64/dbus-1/dbus-daemon-launch-helper -F perm=x -F auid>=500 -F auid!=4294967295 -k T1078_Valid_Accounts
## pkexec invocation
### may indicate privilege escalation CVE-2021-4034
-w /usr/bin/pkexec -p x -k pkexec
## Suspicious shells
-w /bin/ash -p x -k susp_shell
-w /bin/csh -p x -k susp_shell
-w /bin/fish -p x -k susp_shell
-w /bin/tcsh -p x -k susp_shell
-w /bin/tclsh -p x -k susp_shell
-w /bin/xonsh -p x -k susp_shell
-w /usr/local/bin/xonsh -p x -k susp_shell
-w /bin/open -p x -k susp_shell
-w /bin/rbash -p x -k susp_shell
### https://gtfobins.github.io/gtfobins/wish/
-w /bin/wish -p x -k susp_shell
-w /usr/bin/wish -p x -k susp_shell
### https://gtfobins.github.io/gtfobins/yash/
-w /bin/yash -p x -k susp_shell
-w /usr/bin/yash -p x -k susp_shell
# Web Server Actvity
## Change the number "33" to the ID of your WebServer user. Default: www-data:x:33:33
-a always,exit -F arch=b64 -S execve -F euid=33 -k detect_execve_www
### https://clustershell.readthedocs.io/
-w /bin/clush -p x -k susp_shell
-w /usr/local/bin/clush -p x -k susp_shell
-w /etc/clustershell/clush.conf -p x -k susp_shell
### https://github.com/tmux/tmux
-w /bin/tmux -p x -k susp_shell
-w /usr/local/bin/tmux -p x -k susp_shell
## Shell/profile configurations
-w /etc/profile.d/ -p wa -k shell_profiles
-w /etc/profile -p wa -k shell_profiles
-w /etc/shells -p wa -k shell_profiles
-w /etc/bashrc -p wa -k shell_profiles
-w /etc/csh.cshrc -p wa -k shell_profiles
-w /etc/csh.login -p wa -k shell_profiles
-w /etc/fish/ -p wa -k shell_profiles
-w /etc/zsh/ -p wa -k shell_profiles
### https://github.com/xxh/xxh
-w /usr/local/bin/xxh.bash -p x -k susp_shell
-w /usr/local/bin/xxh.xsh -p x -k susp_shell
-w /usr/local/bin/xxh.zsh -p x -k susp_shell
## Injection
### These rules watch for code injection by the ptrace facility.
### This could indicate someone trying to do something bad or just debugging
-a always,exit -F arch=b64 -S ptrace -F a0=0x4 -k code_injection
-a always,exit -F arch=b64 -S ptrace -F a0=0x5 -k data_injection
-a always,exit -F arch=b64 -S ptrace -F a0=0x6 -k register_injection
-a always,exit -F arch=b64 -S ptrace -k tracing
## Anonymous File Creation
### These rules watch the use of memfd_create
### "memfd_create" creates anonymous file and returns a file descriptor to access it
### When combined with "fexecve" can be used to stealthily run binaries in memory without touching disk
-a always,exit -F arch=b64 -S memfd_create -F key=anon_file_create
## Privilege Abuse
### The purpose of this rule is to detect when an admin may be abusing power by looking in user's home dir.
-a always,exit -F dir=/home -F uid=0 -F auid>=1000 -F auid!=-1 -C auid!=obj_uid -k power_abuse
# Socket Creations
# will catch both IPv4 and IPv6
-a always,exit -F arch=b32 -S socket -F a0=2 -k network_socket_created
-a always,exit -F arch=b64 -S socket -F a0=2 -k network_socket_created
-a always,exit -F arch=b32 -S socket -F a0=10 -k network_socket_created
-a always,exit -F arch=b64 -S socket -F a0=10 -k network_socket_created
# Software Management ---------------------------------------------------------
# RPM (Redhat/CentOS)
-w /usr/bin/rpm -p x -k software_mgmt
-w /usr/bin/yum -p x -k software_mgmt
# DNF (Fedora/RedHat 8/CentOS 8)
-w /usr/bin/dnf -p x -k software_mgmt
# YAST/Zypper/RPM (SuSE)
-w /sbin/yast -p x -k software_mgmt
-w /sbin/yast2 -p x -k software_mgmt
-w /bin/rpm -p x -k software_mgmt
-w /usr/bin/zypper -k software_mgmt
# DPKG / APT-GET (Debian/Ubuntu)
-w /usr/bin/dpkg -p x -k software_mgmt
-w /usr/bin/apt -p x -k software_mgmt
-w /usr/bin/apt-add-repository -p x -k software_mgmt
-w /usr/bin/apt-get -p x -k software_mgmt
-w /usr/bin/aptitude -p x -k software_mgmt
-w /usr/bin/wajig -p x -k software_mgmt
-w /usr/bin/snap -p x -k software_mgmt
# PIP(3) (Python installs)
-w /usr/bin/pip -p x -k third_party_software_mgmt
-w /usr/local/bin/pip -p x -k third_party_software_mgmt
-w /usr/bin/pip3 -p x -k third_party_software_mgmt
-w /usr/local/bin/pip3 -p x -k third_party_software_mgmt
-w /usr/bin/pipx -p x -k third_party_software_mgmt
-w /usr/local/bin/pipx -p x -k third_party_software_mgmt
# npm
## T1072 third party software
## https://www.npmjs.com
## https://docs.npmjs.com/cli/v6/commands/npm-audit
-w /usr/bin/npm -p x -k third_party_software_mgmt
# Comprehensive Perl Archive Network (CPAN) (CPAN installs)
## T1072 third party software
## https://www.cpan.org
-w /usr/bin/cpan -p x -k third_party_software_mgmt
# Ruby (RubyGems installs)
## T1072 third party software
## https://rubygems.org
-w /usr/bin/gem -p x -k third_party_software_mgmt
# LuaRocks (Lua installs)
## T1072 third party software
## https://luarocks.org
-w /usr/bin/luarocks -p x -k third_party_software_mgmt
# Pacman (Arch Linux)
## https://wiki.archlinux.org/title/Pacman
## T1072 third party software
-w /etc/pacman.conf -p x -k third_party_software_mgmt
-w /etc/pacman.d -p x -k third_party_software_mgmt
# Special Software ------------------------------------------------------------
## GDS specific secrets
-w /etc/puppet/ssl -p wa -k puppet_ssl
## IBM Bigfix BESClient
-a always,exit -F arch=b64 -S open -F dir=/opt/BESClient -F success=0 -k soft_besclient
-w /var/opt/BESClient/ -p wa -k soft_besclient
## CHEF https://www.chef.io/chef/
-w /etc/chef -p wa -k soft_chef
## Salt
## https://saltproject.io/
## https://docs.saltproject.io/en/latest/ref/configuration/master.html
-w /etc/salt -p wa -k soft_salt
-w /usr/local/etc/salt -p wa -k soft_salt
## Otter
## https://inedo.com/otter
-w /etc/otter -p wa -k soft_otter
## T1081 Credentials In Files
-w /usr/bin/grep -p x -k string_search
-w /usr/bin/egrep -p x -k string_search
-w /usr/bin/ugrep -p x -k string_search
### https://github.com/tmbinc/bgrep
-w /usr/bin/bgrep -p x -k string_search
### https://github.com/BurntSushi/ripgrep
-w /usr/bin/rg -p x -k string_search
### https://github.com/awgn/cgrep
-w /usr/bin/cgrep -p x -k string_search
### https://github.com/jpr5/ngrep
-w /usr/bin/ngrep -p x -k string_search
### https://github.com/vrothberg/vgrep
-w /usr/bin/vgrep -p x -k string_search
### https://github.com/monochromegane/the_platinum_searcher
-w /usr/bin/pt -p x -k string_search
### https://github.com/gvansickle/ucg
-w /usr/bin/ucg -p x -k string_search
### https://github.com/ggreer/the_silver_searcher
-w /usr/bin/ag -p x -k string_search
### https://github.com/beyondgrep/ack3
### https://beyondgrep.com
-w /usr/bin/ack -p x -k string_search
-w /usr/local/bin/ack -p x -k string_search
-w /usr/bin/semgrep -p x -k string_search
## Docker
-w /usr/bin/dockerd -k docker
-w /usr/bin/docker -k docker
-w /usr/bin/docker-containerd -k docker
-w /usr/bin/docker-runc -k docker
-w /var/lib/docker -p wa -k docker
-w /etc/docker -k docker
-w /etc/sysconfig/docker -k docker
-w /etc/sysconfig/docker-storage -k docker
-w /usr/lib/systemd/system/docker.service -k docker
-w /usr/lib/systemd/system/docker.socket -k docker
## Virtualization stuff
-w /usr/bin/qemu-system-x86_64 -p x -k qemu-system-x86_64
-w /usr/bin/qemu-img -p x -k qemu-img
-w /usr/bin/qemu-kvm -p x -k qemu-kvm
-w /usr/bin/qemu -p x -k qemu
-w /usr/bin/virtualbox -p x -k virtualbox
-w /usr/bin/virt-manager -p x -k virt-manager
-w /usr/bin/VBoxManage -p x -k VBoxManage
## Kubelet
-w /usr/bin/kubelet -k kubelet
# ipc system call
# /usr/include/linux/ipc.h
## msgctl
#-a always,exit -S ipc -F a0=14 -k Inter-Process_Communication
## msgget
#-a always,exit -S ipc -F a0=13 -k Inter-Process_Communication
## Use these lines on x86_64, ia64 instead
-a always,exit -F arch=b64 -S msgctl -k Inter-Process_Communication
-a always,exit -F arch=b64 -S msgget -k Inter-Process_Communication
## semctl
#-a always,exit -S ipc -F a0=3 -k Inter-Process_Communication
## semget
#-a always,exit -S ipc -F a0=2 -k Inter-Process_Communication
## semop
#-a always,exit -S ipc -F a0=1 -k Inter-Process_Communication
## semtimedop
#-a always,exit -S ipc -F a0=4 -k Inter-Process_Communication
## Use these lines on x86_64, ia64 instead
-a always,exit -F arch=b64 -S semctl -k Inter-Process_Communication
-a always,exit -F arch=b64 -S semget -k Inter-Process_Communication
-a always,exit -F arch=b64 -S semop -k Inter-Process_Communication
-a always,exit -F arch=b64 -S semtimedop -k Inter-Process_Communication
## shmctl
#-a always,exit -S ipc -F a0=24 -k Inter-Process_Communication
## shmget
#-a always,exit -S ipc -F a0=23 -k Inter-Process_Communication
## Use these lines on x86_64, ia64 instead
-a always,exit -F arch=b64 -S shmctl -k Inter-Process_Communication
-a always,exit -F arch=b64 -S shmget -k Inter-Process_Communication
# High Volume Events ----------------------------------------------------------
## Disable these rules if they create too many events in your environment
## Common Shells
-w /bin/bash -p x -k susp_shell
-w /bin/dash -p x -k susp_shell
-w /bin/busybox -p x -k susp_shell
-w /bin/zsh -p x -k susp_shell
-w /bin/sh -p x -k susp_shell
-w /bin/ksh -p x -k susp_shell
## Root command executions
-a always,exit -F arch=b64 -F euid=0 -F auid>=1000 -F auid!=-1 -S execve -k rootcmd
## File Deletion Events by User
-a always,exit -F arch=b64 -S rmdir -S unlink -S unlinkat -S rename -S renameat -F auid>=1000 -F auid!=-1 -k delete
## File Access
### Unauthorized Access (unsuccessful)
-a always,exit -F arch=b64 -S creat -S open -S openat -S open_by_handle_at -S truncate -S ftruncate -F exit=-EACCES -F auid>=1000 -F auid!=-1 -k file_access
-a always,exit -F arch=b64 -S creat -S open -S openat -S open_by_handle_at -S truncate -S ftruncate -F exit=-EPERM -F auid>=1000 -F auid!=-1 -k file_access
### Unsuccessful Creation
-a always,exit -F arch=b64 -S mkdir,creat,link,symlink,mknod,mknodat,linkat,symlinkat -F exit=-EACCES -k file_creation
-a always,exit -F arch=b64 -S mkdir,link,symlink,mkdirat -F exit=-EPERM -k file_creation
### Unsuccessful Modification
-a always,exit -F arch=b64 -S rename -S renameat -S truncate -S chmod -S setxattr -S lsetxattr -S removexattr -S lremovexattr -F exit=-EACCES -k file_modification
-a always,exit -F arch=b64 -S rename -S renameat -S truncate -S chmod -S setxattr -S lsetxattr -S removexattr -S lremovexattr -F exit=-EPERM -k file_modification
## 32bit API Exploitation
### If you are on a 64 bit platform, everything _should_ be running
### in 64 bit mode. This rule will detect any use of the 32 bit syscalls
### because this might be a sign of someone exploiting a hole in the 32
### bit API.
-a always,exit -F arch=b32 -S all -k 32bit_api
# Make The Configuration Immutable --------------------------------------------
##-e 2Ahora solo tienes que guardar el archivo pulsando ESC y dando a :wq!
Y ya tienes tus reglas. ¿Algo más? Vamos a comprobar si todas las reglas están cargadas:
sudo augenrules --checkTe va a salir algo como esto: /sbin/augenrules: Rules have changed and should be updated.
Pues las cargamos:
sudo augenrules --loadYa hora comprobamos si todas funcionan correctamente con el comando:
sudo auditctl -sY te puede salir algo como esto:
enabled 1
failure 1
pid 604
rate_limit 0
backlog_limit 8192
lost 0
backlog 0
backlog_wait_time 60000
backlog_wait_time_actual 2532
loginuid_immutable 0 unlocked
Error sending add rule data request (Operation not supported)
There was an error in line 81 of /etc/audit/rules.d/audit.rules
Error sending add rule data request (Operation not supported)
There was an error in line 82 of /etc/audit/rules.d/audit.rules
Error sending add rule data request (Operation not supported)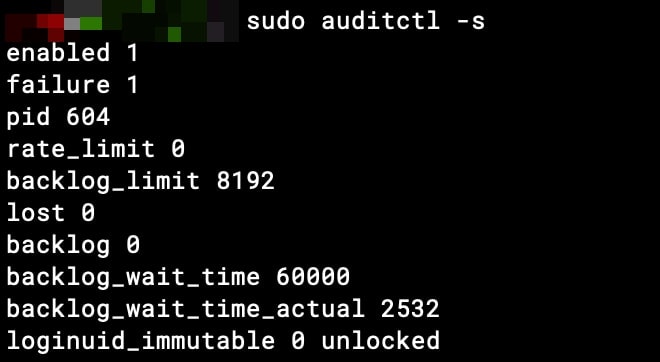
Nota: Es importante tener configurado lo siguiente en estas reglas (al principio del archivo):
- # Remove any existing rules
- -D
- # Buffer Size
- -b 8192
- # Failure Mode: possible values: 0 (silent), 1 (printk, print a failure message), 2 (panic, halt the system)
- -f 1
- # Ignore errors: caused by users or files not found in the local environment
- -i
Quitamos reglas anteriores, aumentamos el tamaño del buffer de memoria y ponemos el modo de fallos en 1. ¡Ojo! Si lo pones en 2 tu sistema se va al carajo. E ignoramos posibles errores para que el sistema siga funcionando en caso de reglas mal configuradas.
Tienes que revisar las reglas que están cargando mal en las líneas que te indica. Puedes comentarlas con almohadillas (#). Y ahora puedes revisar las reglas que han sido cargadas en Auditd:
sudo auditctl -l¿Quieres reiniciar el servicio de auditd en RHEL o Rocky Linux? Seguro que te vas a encontrar un problema como este: «Failed to restart auditd.service: Operation refused, unit auditd.service may be requested by dependency only (it is configured to refuse manual start/stop). See system logs and ‘systemctl status auditd.service’ for details.«

Lo que tienes que hacer es editar ela rchivo siguiente con vi:
vi /usr/lib/systemd/system/auditd.serviceY cambias el parámetro siguiente con este valor: RefuseManualStop=no
Ahora ejecutas:
sudo systemctl daemon-reloadPuedes comprobar el estado del servicio con:
sudo systemctl status auditd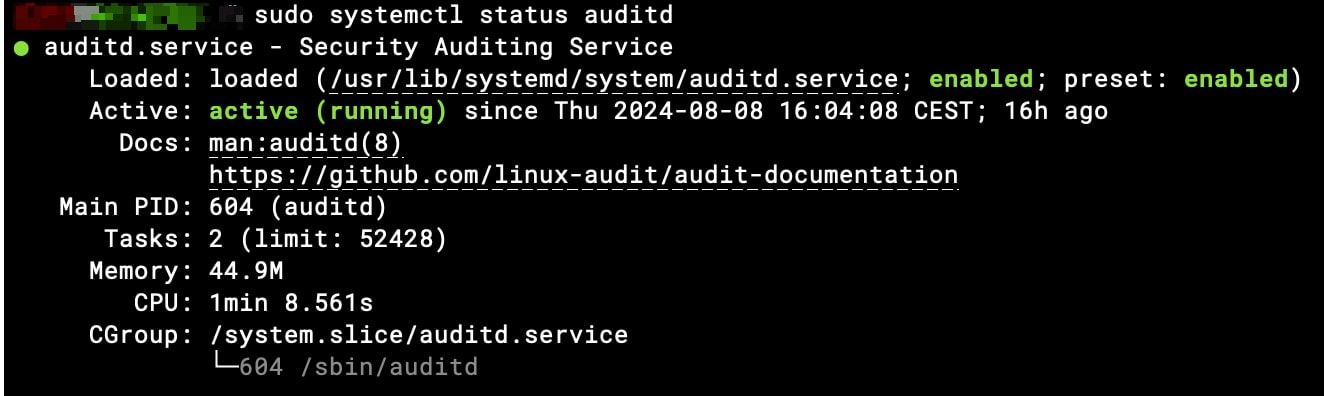
Comandos útiles
ausearch: buscamos en los logs
Tienes dos bastante útiles, uno para buscar en los logs de auditd y otro para crear reportes:
sudo ausearch -i -k nombre_regla¿Cuál es el nombre de la regla? Viene al final de cada una con el flag -k, por ejemplo -k susp_activity
Si quieres buscar todos los eventos que ha recogido la regla o reglas susp_activity, solo tienes que poner:
sudo ausearch -i -k susp_activity¿Cambios en usuarios o grupos? Siempre nos basamos en el nombre de las reglas que hemos metido en audit.rules.
sudo ausearch -i -k user_modification
sudo ausearch -i -k group_modificationMás ejemplos:
#Actividad usuario
ausearch -ua root -i
ausearch -ua root -ts yesterday -te now -i
#Procesos activos
ausearch -p PID(lo_cambias)aureport: generamos informes
Aquí tienes unos cuantos ejemplos:
#Informe resumido de eventos fallidos para todos los usuarios
aureport -u --failed --summary -i
#Todos los intentos de inicio de sesión fallidos por cada usuario del sistema
aureport --login --summary -i
#Todos los eventos fallidos.
aureport --failed
#Eventos ejecutables
aureport -x
#Informe sobre todos los eventos relacionados con los intentos de autenticación para todos los usuarios
aureport -au -i
#Informes durante un período de tiempo específico; el -ts define la fecha/hora de inicio y -te establece una fecha/hora de finalización.
aureport -ts yesterday -te now --summary -i Creamos un cron para que se ejecute todos los días
Y te va a mandar un informe resumido de algunas cosas importantes para que lo veas de un vistazo:
9 1 * * * /sbin/aureport -ts yesterday --summary --input-logs -i 2>&1 | mail -s 'Informe AUDITD' [email protected]Que te va a mandar algo como esto:
Summary Report
======================
Range of time in logs: 01/01/1970 01:00:00.000 - 08/09/2024 01:09:02.544
Selected time for report: 08/08/2024 00:00:00 - 08/09/2024 01:09:02.544
Number of changes in configuration: 4
Number of changes to accounts, groups, or roles: 0
Number of logins: 0
Number of failed logins: 0
Number of authentications: 150
Number of failed authentications: 0
Number of users: 17
Number of terminals: 3
Number of host names: 173
Number of executables: 36
Number of commands: 51
Number of files: 1232
Number of AVC's: 0
Number of MAC events: 0
Number of failed syscalls: 8517
Number of anomaly events: 2
Number of responses to anomaly events: 0
Number of crypto events: 0
Number of integrity events: 0
Number of virt events: 0
Number of keys: 24
Number of process IDs: 5410
Number of events: 49997¿Más reglas para Auditd?
Pues si tienes instalado OpenSCAP, este programa te va a dar unas cuantas recomendaciones de reglas que probablemente no cumples en tu sistema. Tiene truco. Es posible que no las hayas puesto exactamente como ellos quieren, pero con el anterior archivo de reglas de que te he comentado estás más que cubierto.
En mi caso, que me las he revisado una a una, he añadido unas cuantas reglas que han recomendado desde este programa:
#Record Any Attempts to Run chacl
-a always,exit -F path=/usr/bin/chacl -F perm=x -F auid>=1000 -F auid!=unset -F key=privileged
#Record Any Attempts to Run setfacl
-a always,exit -F path=/usr/bin/setfacl -F perm=x -F auid>=1000 -F auid!=unset -F key=privileged
#Record Any Attempts to Run chcon
-a always,exit -F path=/usr/bin/chcon -F perm=x -F auid>=1000 -F auid!=unset -F key=privileged
#Ensure auditd Collects File Deletion Events by User - rename
-a always,exit -F arch=b64 -S rename -F auid>=1000 -F auid!=unset -F key=delete
#Ensure auditd Collects File Deletion Events by User - renameat
-a always,exit -F arch=b64 -S renameat -F auid>=1000 -F auid!=unset -F key=delete
#Ensure auditd Collects File Deletion Events by User - unlink
-a always,exit -F arch=b64 -S unlink -F auid>=1000 -F auid!=unset -F key=delete
#Ensure auditd Collects File Deletion Events by User - unlinkat
-a always,exit -F arch=b64 -S unlinkat -F auid>=1000 -F auid!=unset -F key=delete
#Ensure auditd Collects Information on Kernel Module Unloading - create_module
-a always,exit -F arch=b64 -S create_module -F key=module-change
#Ensure auditd Collects Information on Kernel Module Unloading - delete_module
-a always,exit -F arch=b64 -S delete_module -F auid>=1000 -F auid!=unset -F key=modules
#Ensure auditd Collects Information on Kernel Module Loading and Unloading - finit_module
-a always,exit -F arch=b64 -S finit_module -F auid>=1000 -F auid!=unset -F key=modules
#Ensure auditd Collects Information on Kernel Module Loading - init_module
-a always,exit -F arch=b64 -S init_module -F auid>=1000 -F auid!=unset -F key=modules
#Ensure auditd Collects Information on Kernel Module Loading and Unloading - query_module
-a always,exit -F arch=b64 -S query_module -F auid>=1000 -F auid!=unset -F key=modules
#Record Attempts to Alter Logon and Logout Events - faillock
-w /var/run/faillock -p wa -k logins
#Record Events that Modify the System's Mandatory Access Controls in usr/share
-w /usr/share/selinux/ -p wa -k MAC-policyTe recomiendo que utilices OpenSCAP y lo compruebes tú mismo en tu sistema, que te pueden dar resultados diferentes. También te recomiendo que uses Lynis.
Conclusión
tienes que activar y configurar correctamente Auditd si quieres llevar un buen control de todo lo que pasa en tu sistema Linux, y la mejor manera de hacerlo es instalar un buen conjunto de reglas para que el sistema vaya recogiendo información que luego tú vas a tener que procesar.
Las reglas que te he recomendado son más que suficientes para un sistema estándar, pero siempre puedes utilizar OpenSCAP y que te recomiende otras tantas. Las tienes que revisar una a una para que no haya duplicados. Es lo único con lo que tienes que tener cuidado.
También recomiendan mucho usar https://github.com/threathunters-io/laurel. LAUREL es un plugin de procesamiento para auditd que genera registros de auditoría útiles y enriquecidos basados en JSON. Todavía no lo he instalado.
¿Más cosas que puedes instalar en tu servidor? Te recomiendo que uses logwatch para controlar tus logs, instalar RKhunter para comprobar Rootkits, Maldet y ClamAV para malware y virus (para servidores de correo), instalar un Firewall como CSF, un HIDS como OSSEC o mejorar la seguridad de SSH, Apache o MariaDB o los parámetros del Kernel.
Referencias:
- https://www.redhat.com/sysadmin/configure-linux-auditing-auditd
- https://medium.com/@boristheblade1/configuring-auditd-in-linux-6d1f6e100079
- https://linux-audit.com/configuring-and-auditing-linux-systems-with-audit-daemon/
- https://linux.die.net/man/8/auditctl
- https://www.digitalocean.com/community/tutorials/how-to-use-the-linux-auditing-system-on-centos-7